Miscellaneous: Setting up SSH
To enable secure access to your Cisco device, you can use SSH instead of Telnet. SSH uses encryption to secure data from eavesdropping.
To enable SSH, the following steps are required:
1. set up a hostname and and a domain name
2. configure local username and password
3. generate RSA public and private keys
4. allow only SSH access
The following example shows the configuration of the first three steps:
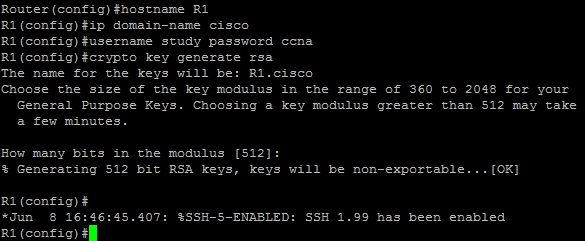
First, we have defined the device hostname by using the hostname R1 command. Next, we have defined the domain name by using the ip domain-name cisco command. After that, the local user is created by using the username study password ccna command. Next, we need to enable only SSH access to a device. This is done by using the transport input ssh command:

If we use the transport input ssh command, the telnet access to the device is automatically disabled.
NOTE – you should use the more recent version of the protocol, SSH version 2. This is done by using the ip ssh version 2 global configuration command.
